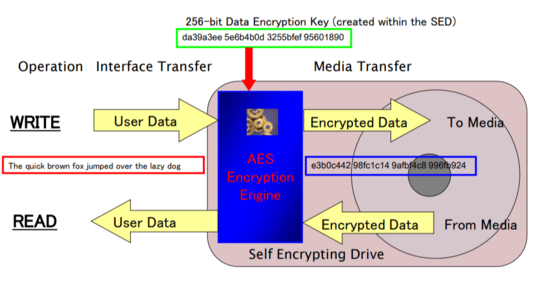
SED (Self-Encrypting Drives)
A self-encrypting drive (SED) is a hard disk drive (HDD) or solid-state drive (SSD) designed to automatically encrypt and decrypt drive data without the need for user input or disk encryption software. Samsung, Seagate, and Toshiba, have SEDs on the market today.
Many self-encrypting drives available today implement the OPAL and Enterprise standards developed by the Trusted Computing Group (TCG).
SEDs use an on-board cryptoprocessor to encrypt and decrypt your data.
Unlike with software-based disk encryption, the DEK never makes its way to the host system’s random-access memory (RAM), where it can be accessed by attackers using a cold boot or software-level attack.
SED on Linux
msed and OpalTool, the two known Open Source code bases available for self-encrypting drives support on Linux merged to form sedutil
For devices connected via SATA, libata.allow_tpm must be set to 1 (true) in order to use sedutil. Either add libata.allow_tpm=1 to the kernel parameters, or by setting /sys/module/libata/parameters/allow_tpm to 1 on a running system. [1]
- This page shows how to compile and setup sedutil on Ubuntu
- Using Self-Encrypting Drives on Linux page shows high level sedutil-cli usage
# Check hdd support SED using hdparm to check "security" related output
sudo hdparm -I /dev/xxxx
Check if you have OPAL compliant disks using sedutil-cli
# sedutil-cli --scan